Banning or Backdooring Encryption Will Break the Internet
It seems like every other day, a lawmaker from a major democratic country is set to introduce some legislation which would break the internet as we know it. While these laws and treaties may be well-intentioned (crafted in the name of "security" or "protecting artists"), they're being written by people who have a deep, DEEP ignorance of how the internet and technology actually works. Such people don't understand that the consequence of their laws, as written, could be the destruction of the web. Why didn't these lawmakers and law-enforcers actually consult with technologically knowledgeable professionals before going off half-cocked? This is like a government creating rules about how bridges are to be built without consulting a single engineer. It's not just stupid, it's dangerous.
But I digress... Today's existential threat to the internet: the banning of "strong encryption". I use quote-marks because, as you might imagine, this is a layperson's term that doesn't actually mean anything from a technical standpoint. For me to fully explain, we'll need to go back a couple of years.
In 2013, we learned from NSA whistleblower Edward Snowden that encryption works. While the NSA may be able to hack an endpoint device (your phone, computer, etc) and steal data from it, they can't intercept data in transit when a connection is encrypted. This annoys and frustrates intelligence agencies, who seem to feel that they should be able to access anything they want at will. As I stated in my September article, The Fallacy of the "Secret Master Key", FBI director Jim Comey publicly called for encryption backdoors for law enforcement as recently at this past July. Likewise, UK Prime Minister David Cameron wants to ban encryption unless there's a secret backdoor for the government.
Again, the purpose of my "Secret Master Key" article was to point out that the whole concept of "a backdoor that only the good guys can use" is totally flawed. Simply put, when a lock has a built-in "backdoor" for "the good guys", it's only a backdoor as long as it is kept secret. As soon as anyone - vandal hackers, criminals, and yes, terrorists - discover how to access the backdoor, or get a copy of the private key, the backdoor becomes a critical security vulnerability affecting a huge number of devices. Secrets are hard to keep, and so those kind of security leaks (like the leaked TSA keys) do and will happen.
In their draconian "Investigatory Powers Bill", the UK government has said that while they have no plan to ban encryption outright, they will require all encryption, including that used by banks, to be decipherable. In essence, it should have a backdoor - this makes encryption broken by design. Both malicious hackers and security researchers have a history of discovering massive security holes in software, which were created accidentally by programmers. Uncovering a security hole that everyone knows exists and which was purposefully built-in to software would undoubtedly be much more trivial to discover and exploit.
So you see, there is no such thing as "strong encryption", only "encryption that works", and "encryption that doesn't work" - That is neither understatement nor hyperbole. Mandating backdoors into encryption would be the most disastrous thing to ever happen to the internet. Period.
First and foremost, ordinary citizens would find themselves the victims of frequent monetary and identity theft. Without strong encryption, our online banking and credit card purchases are even more vulnerable to interception by hackers, putting our bank and credit card data into the hands of criminals. The same goes for enormous amounts of sensitive personal data - taxes, medical, insurance - currently submitted to governments and other privileged parties under SSL-encrypted HTTPS connections.
The private sector also relies heavily on encryption for day-to-day activities. As a systems administrator, I use SSH to access the systems I administrate from outside the office. Without reliable encryption technology, my administrative credentials could potentially be intercepted, and used to wreak havoc on our small business by a malicious party (data extortion is already a very real threat).
Putting small-to-medium businesses at a much greater risk of security breaches is one thing, but broken encryption would make it nearly impossible for massive networks like Facebook, Amazon, Apple, or Google to operate effectively. While neither I nor the average IT person knows much about the inner workings of such complex proprietary networks, it's difficult to imagine being able to administrate or even implement them without lots of encrypted connections. As it stands, Sony, GoDaddy, and Apple have all suffered serious security breaches within the past few years. It's hard enough for a major enterprise to deal with IT security without their most important tool being deliberately hamstrung by the government.
But the most damning nail in the coffin for "reversible encryption" rhetoric comes from Kim Zetter over at Wired, who pointed out that while banning/backdooring encryption would cripple our infrastructure, it won't stop criminals from homebrewing their own encryption methods. Her article quotes Nate Cardozo of the Electronic Frontier Foundation:
This is exactly the kind of world you can expect to be facing. Kim Zettor's excellent Wired article, along with one by Trevor Timm at the Guardian, make the case that intelligence agencies throughout the world see the November 2015 Paris attacks as an opportunity to frighten the populace into banning/breaking encryption. It has become a familiar story: a distasteful attempt by authorities to exploit a terrible human tragedy as a springboard for a Machiavellian power-grab.
It's always tempting for some to make the argument that the righteous have nothing to hide - a fallacious axiom that is usually trotted out by advocates of mass surveillance. In the case of computer science, digital security, and IP networking, it is anathema. Without a guarantee of security, we won't be able to properly operate anything, and we will be more vulnerable to attack than ever.
Hopefully someone will point this out before lawmakers push blindly forward with their anti-encryption agenda. Yet, I have a pit in my stomach: stopping politicians from doing incredibly stupid things requires pushback from the voting public. Encryption isn't exactly a "sexy" topic, and I doubt the average person realizes how much their day-to-day life, their privacy and safety, depend on it.
I hope this article has helps people to understand the seriousness of this debate. Otherwise, we may very well let our own ignorance destroy the technologies we've come to depend on.
EDIT 2: Forbes reports that the Information Technology Industry Council (ITI), whose membership is a who's-who of the tech industry (Apple, Google, Microsoft, Facebook, Symantec, etc) has released an open letter to President Obama explaining that what I've extolled here: backdooring encryption will break it. It's worth a read.
EDIT: For those of us who are a certain age, here's one last thought on "back doors":
image compiled using vector art by Leremy/Shutterstock
But I digress... Today's existential threat to the internet: the banning of "strong encryption". I use quote-marks because, as you might imagine, this is a layperson's term that doesn't actually mean anything from a technical standpoint. For me to fully explain, we'll need to go back a couple of years.
In 2013, we learned from NSA whistleblower Edward Snowden that encryption works. While the NSA may be able to hack an endpoint device (your phone, computer, etc) and steal data from it, they can't intercept data in transit when a connection is encrypted. This annoys and frustrates intelligence agencies, who seem to feel that they should be able to access anything they want at will. As I stated in my September article, The Fallacy of the "Secret Master Key", FBI director Jim Comey publicly called for encryption backdoors for law enforcement as recently at this past July. Likewise, UK Prime Minister David Cameron wants to ban encryption unless there's a secret backdoor for the government.
Again, the purpose of my "Secret Master Key" article was to point out that the whole concept of "a backdoor that only the good guys can use" is totally flawed. Simply put, when a lock has a built-in "backdoor" for "the good guys", it's only a backdoor as long as it is kept secret. As soon as anyone - vandal hackers, criminals, and yes, terrorists - discover how to access the backdoor, or get a copy of the private key, the backdoor becomes a critical security vulnerability affecting a huge number of devices. Secrets are hard to keep, and so those kind of security leaks (like the leaked TSA keys) do and will happen.
In their draconian "Investigatory Powers Bill", the UK government has said that while they have no plan to ban encryption outright, they will require all encryption, including that used by banks, to be decipherable. In essence, it should have a backdoor - this makes encryption broken by design. Both malicious hackers and security researchers have a history of discovering massive security holes in software, which were created accidentally by programmers. Uncovering a security hole that everyone knows exists and which was purposefully built-in to software would undoubtedly be much more trivial to discover and exploit.
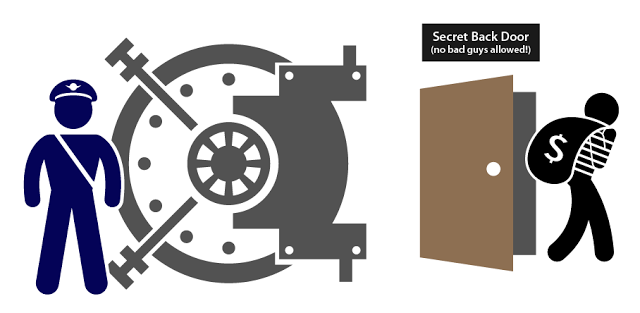 |
| Yes, it's THIS dumb. |
So you see, there is no such thing as "strong encryption", only "encryption that works", and "encryption that doesn't work" - That is neither understatement nor hyperbole. Mandating backdoors into encryption would be the most disastrous thing to ever happen to the internet. Period.
First and foremost, ordinary citizens would find themselves the victims of frequent monetary and identity theft. Without strong encryption, our online banking and credit card purchases are even more vulnerable to interception by hackers, putting our bank and credit card data into the hands of criminals. The same goes for enormous amounts of sensitive personal data - taxes, medical, insurance - currently submitted to governments and other privileged parties under SSL-encrypted HTTPS connections.
The private sector also relies heavily on encryption for day-to-day activities. As a systems administrator, I use SSH to access the systems I administrate from outside the office. Without reliable encryption technology, my administrative credentials could potentially be intercepted, and used to wreak havoc on our small business by a malicious party (data extortion is already a very real threat).
Putting small-to-medium businesses at a much greater risk of security breaches is one thing, but broken encryption would make it nearly impossible for massive networks like Facebook, Amazon, Apple, or Google to operate effectively. While neither I nor the average IT person knows much about the inner workings of such complex proprietary networks, it's difficult to imagine being able to administrate or even implement them without lots of encrypted connections. As it stands, Sony, GoDaddy, and Apple have all suffered serious security breaches within the past few years. It's hard enough for a major enterprise to deal with IT security without their most important tool being deliberately hamstrung by the government.
But the most damning nail in the coffin for "reversible encryption" rhetoric comes from Kim Zetter over at Wired, who pointed out that while banning/backdooring encryption would cripple our infrastructure, it won't stop criminals from homebrewing their own encryption methods. Her article quotes Nate Cardozo of the Electronic Frontier Foundation:
“There’s no way of preventing a terrorist from installing a Russian [encryption] app or a Brasilian app ... The US or UK government could mandate [backdoors], but Open Whisper Systems is not going to put in a backdoor in their product period and neither is PGP. So as soon as a terrorist is sophisticated enough to know how to install that, any backdoor is going to be defeated.”Imagine a world where door locks are outlawed, under the pretence that police or first responders need to be able to get anywhere quickly in an emergency. Crime would be rampant, theft would be commonplace. There would be no privacy, no security, and no safety.
This is exactly the kind of world you can expect to be facing. Kim Zettor's excellent Wired article, along with one by Trevor Timm at the Guardian, make the case that intelligence agencies throughout the world see the November 2015 Paris attacks as an opportunity to frighten the populace into banning/breaking encryption. It has become a familiar story: a distasteful attempt by authorities to exploit a terrible human tragedy as a springboard for a Machiavellian power-grab.
It's always tempting for some to make the argument that the righteous have nothing to hide - a fallacious axiom that is usually trotted out by advocates of mass surveillance. In the case of computer science, digital security, and IP networking, it is anathema. Without a guarantee of security, we won't be able to properly operate anything, and we will be more vulnerable to attack than ever.
Hopefully someone will point this out before lawmakers push blindly forward with their anti-encryption agenda. Yet, I have a pit in my stomach: stopping politicians from doing incredibly stupid things requires pushback from the voting public. Encryption isn't exactly a "sexy" topic, and I doubt the average person realizes how much their day-to-day life, their privacy and safety, depend on it.
I hope this article has helps people to understand the seriousness of this debate. Otherwise, we may very well let our own ignorance destroy the technologies we've come to depend on.
EDIT 2: Forbes reports that the Information Technology Industry Council (ITI), whose membership is a who's-who of the tech industry (Apple, Google, Microsoft, Facebook, Symantec, etc) has released an open letter to President Obama explaining that what I've extolled here: backdooring encryption will break it. It's worth a read.
EDIT: For those of us who are a certain age, here's one last thought on "back doors":
image compiled using vector art by Leremy/Shutterstock
